A Brief Colonial History Of Ceylon(SriLanka)
Sri Lanka: One Island Two Nations
A Brief Colonial History Of Ceylon(SriLanka)
Sri Lanka: One Island Two Nations
(Full Story)
Search This Blog
Back to 500BC.
==========================
Thiranjala Weerasinghe sj.- One Island Two Nations
?????????????????????????????????????????????????Friday, June 11, 2021
X-Press Pearl disaster Will SL authorities sink or swim in compensation claim?
 |
Wednesday, 9 June 2021
Cyber security is a fast-changing and highly-technical area so directors must rely on their IT teams for clarity. However, the more boards and risk committees I speak to the more I realise that directors and IT security teams are not even reading from the same book, let alone being on the same page. Ironically, unlike most issues, both sides of the table agree that cyber security is important. This begs the question, why are successful cyber-attacks continuing?
The simple answer is the lack investment in security because boards do not have a way to measure ROI of cyber security. When companies do not measure their security posture they do not know if an investment had any impact. So, without a clear view of their cyber risk companies are left shooting blind and hoping for the best.
Dangerous miscommunications
For a director to make good decisions and honour their fiduciary duty they need to weigh the risks and benefits of any investment, including security. Unfortunately, due to differences in jargon and the lack of a reporting standard the severity of security issues is rarely communicated accurately.
When severity is constantly overstated IT teams start looking like the boy who cried wolf one too many times and mistrust builds. When risks are understated, and incidents occur IT teams look incompetent. Therefore, it is no surprise that IT risk meetings are unproductive, confusing, and regularly devolve into grandstanding, fear tactics and politics.
Obviously, neither of these situations are desirable, the company has either overinvested resources that could have been used elsewhere or is left vulnerable to cyber-attacks.
How do we measure cyber risk?
Regular security testing by external auditors has finally become common place, at least in publicly listed companies. But this has led to an information overload which often overwhelms IT departments. A few hundred pages of security issues are delivered by an auditor every three months and IT managers are told to fix everything.
They now must analyse and prioritise a few thousand issues for fixing and coordinate with internal staff and external vendors. Manually managing this process often takes so long that the next audit starts before they are halfway done resulting in many issues slipping through the cracks, leaving the company open to attack.
This is where modern risk-based vulnerability management (RBVM) solutions come in. They carry out three main functions:
Automatic analysis and prioritisation of issues found in security audits.
Tracking the status of fixes. Issues are assigned to the responsible party with suggestions and deadlines.
Gathering threat intelligence to find out which of the issues in your systems are being used by cyber criminals to attack other organisations.
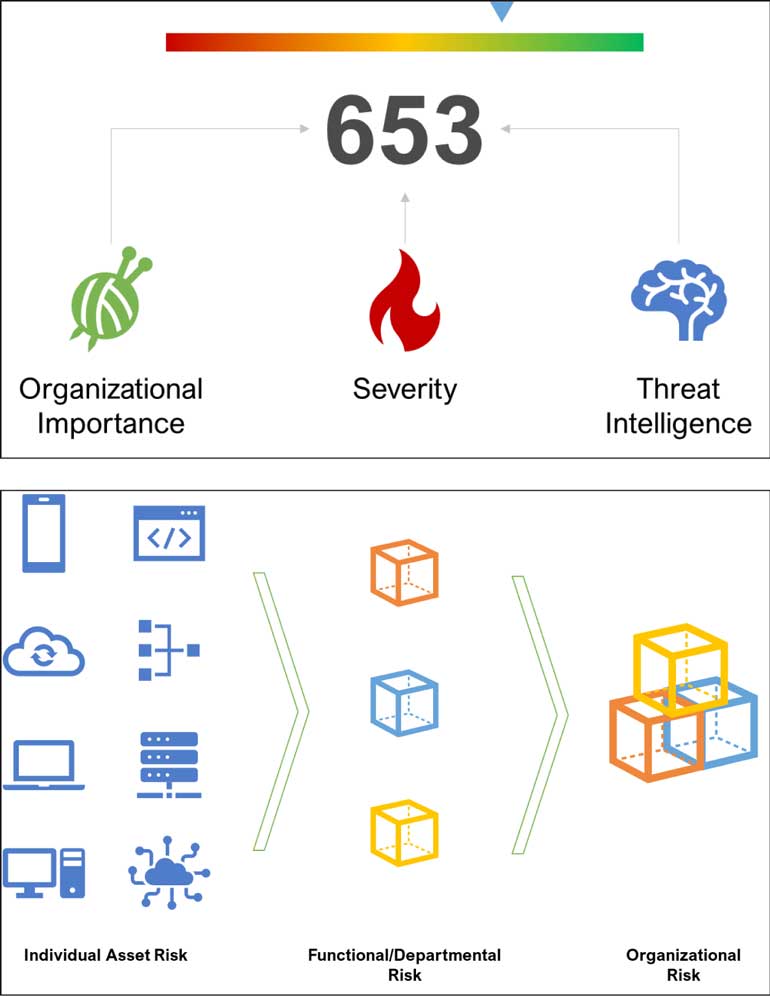
In summary, RBVM crunches all your security data automatically to make it understandable, transparent, and actionable. It tells you exactly what is important to fix and when to fix it based on the global threat landscape, rather than relying on the subjective opinions of a few people.
Objective risk scoring
Since RBVM systems unify all security information they can provide an objective risk score for the whole organisation. This risk score is a metric that is simple to understand and communicate, like a credit score.
Any changes in the score can easily be attributed to the discovery or fixing of security issues. It also takes into real world intelligence, so that the score will automatically update, for example if a vulnerability affecting one of your systems is disclosed by the manufacturer. In this way, knowing your cyber-risk becomes simple.
With an objective measure in place, ROI calculations become much easier. If you want to improve your score by 30 points, you know exactly which systems need to be upgraded and whether you need more resources to do it. You also know how much you stand to lose if that system is compromised. This means the IT risk meetings do not require jargon anymore.
What gets measured, gets managed – what gets managed, gets done
Collaboration, accountability and transparency
Cyber security is a collaborative effort; IT, HR, boards, risk teams, auditors, regulators, insurers, customers, and external service providers must all be aligned to secure an organisation. Coordinating this effort is a monumental task that RBVM helps to automate. By adding all stakeholders to the same platform, organisations get an unprecedented level of transparency.
Our customers have been able to identify and prove that certain vendors have not updated systems in years and legally enforced SLAs. Some found that certain branches have not been following security guidelines and took disciplinary actions.
On the positive side, other customers have been able to quantify their cyber risk to insurers and negotiated better premiums. Others have cut down their regulatory and audit reporting time to a few minutes. Some board members even run their own reports whenever a high-profile security event is in the press, to see if the same issue exists in their company, without any intervention from IT.
Efficient decision making
Having a KPI for cyber security means even non-technical board members can now understand their cyber risk and therefore allocate resources better. IT departments are also become more transparent and fix issues faster with the help of automation. Meetings become more streamlined since reporting is simple; X resources were given last month, was target Y achieved and if not, why.
Conclusion
Cyber security incidents have ballooned over the last few years due to digitalisation and the increasing profitability of cyber-crime. Threat actors are always on the lookout for vulnerable systems. If these issues are not identifying and fixed proactively, an attack is inevitable.
To get ahead of attackers, measure your cyber risk as soon as possible and continuously monitor it. Hold all your stakeholders accountable for the safety of your organisation. Your customers and shareholders will thank you.
[The writer is a Director in a company which specialises in Risk-based Vulnerability Management (RBVM). He is an entrepreneur working in the fields of cyber security, fintech and ecommerce. After six years of working at e-commerce start-ups in Sri Lanka and Malaysia, he now helps Sri Lankan companies improve their e-commerce strategies, digital payments infrastructure and cyber security posture. He can be reached on imesh@teksek. lk via email or @imesh_l on Twitter.]


